Security & Scams
Benefits of Using Innocams
Published
5 months agoon
By
Saad
Welcome to the world of modern surveillance where peace of mind meets cutting-edge technology. Imagine having the power to monitor your home or business from anywhere in the world with just a few clicks on your smartphone. Say hello to Innocams – your ultimate solution for seamless security and remote monitoring. Let’s dive into the myriad benefits that come with using Innocams and how it can revolutionize the way you keep an eye on what matters most to you.
What is Innocams and How Does it Work?
Innocams is a cutting-edge video surveillance system designed to provide seamless security solutions for both residential and commercial properties. This innovative technology allows users to monitor their premises remotely through high-definition cameras equipped with advanced features.
The workings of Innocams are simple yet sophisticated – the cameras capture real-time footage which is then transmitted wirelessly to a central hub or cloud storage. Users can access this live feed through a user-friendly mobile app or web portal, allowing them to keep an eye on their property from anywhere in the world.
With motion detection capabilities and night vision functionality, Innocams ensures round-the-clock surveillance without any blind spots. The system also offers options for video recording and playback, giving users peace of mind knowing that they can review footage whenever needed.
Innocams revolutionizes the way we approach security by providing an efficient and reliable monitoring solution tailored to modern needs.
The Advantages of Using Innocams:
Enhanced Security: Innocams provides a reliable way to monitor your property in real-time, offering peace of mind and ensuring the safety of your loved ones and belongings. With features like motion detection and night vision, you can rest assured that your premises are secure 24/7.
Remote Monitoring: Whether you’re at work, on vacation, or simply away from home, Innocams allows you to keep an eye on things remotely through its user-friendly mobile app. Stay connected and informed no matter where you are, giving you the flexibility and convenience to check in whenever needed.
Cost-Effective Solution: Investing in Innocams is a cost-effective alternative to traditional security systems. With easy installation and no monthly fees, it offers an affordable way to enhance your security measures without breaking the bank. Save money without compromising on quality or effectiveness with this smart surveillance solution.
A. Enhanced Security
When it comes to security, Innocams offers peace of mind like no other. With advanced features such as motion detection and real-time alerts, you can rest assured knowing that your property is constantly being monitored. Whether you’re away on vacation or just at work, Innocams keeps a watchful eye on what matters most.
The high-definition video quality allows for clear footage, making it easier to identify any potential threats or intruders. In addition, the two-way audio feature enables you to communicate with anyone on the other end of the camera – a valuable tool in emergencies or simply for everyday convenience.
Innocams also provides encrypted data transmission, ensuring that your footage remains secure and private. This added layer of protection gives you confidence in knowing that your personal information is safe from prying eyes.
B. Remote Monitoring
Remote monitoring is a key benefit of using Innocams. With this feature, you can access live video feeds from your cameras anytime and anywhere. Whether you’re at work, on vacation, or simply out running errands, you can keep an eye on your property with just a few clicks on your smartphone or computer.
This real-time access allows you to stay informed about what’s happening in your home or business even when you’re not physically there. You can quickly check in to see if everything is as it should be or receive instant alerts if any suspicious activity is detected.
The ability to remotely monitor your premises provides peace of mind and helps you feel more connected to your space no matter where you are. Whether it’s keeping an eye on pets while away or ensuring the safety of loved ones, remote monitoring offers convenience and security at your fingertips.
C. Cost-Effective Solution
Looking to enhance your security system without breaking the bank? Look no further than Innocams. This innovative solution offers cost-effective monitoring options that won’t drain your budget.
With Innocams, you can enjoy all the benefits of a high-quality security system at a fraction of the cost. Say goodbye to expensive installation fees and monthly subscriptions – Innocams provides affordable surveillance solutions tailored to your needs.
By opting for Innocams, you not only save money upfront but also in the long run. Its efficient technology ensures minimal maintenance costs and maximum savings over time.
Don’t compromise on quality just because you’re working with a limited budget. Invest in Innocams for a reliable and economical security solution that delivers peace of mind without burning a hole in your pocket.
How to Set Up and Use Innocams
Setting up and using Innocams is a straightforward process that ensures optimal security and peace of mind. To begin, choose a strategic location to install the cameras for maximum coverage. Ensure they are placed at key points to monitor activity effectively.
Next, connect the cameras to a power source and ensure they have a stable internet connection for seamless remote access. Install the Innocams app on your smartphone or computer to easily view live feeds and recordings from anywhere at any time.
Once everything is set up, customize the settings according to your preferences, such as motion detection alerts or scheduled recording times. Familiarize yourself with the user-friendly interface to make adjustments effortlessly.
Regularly check the camera angles and image quality to guarantee clear footage. In case of any technical issues, refer to the user manual or contact customer support for assistance. Enjoy enhanced security and convenience with Innocams in just a few simple steps!
Case Studies: Real-Life Examples of Successful Implementation of Innocams
Imagine a bustling office space where employees work diligently to meet deadlines and deliver top-notch results. Thanks to Innocams, the security team can keep a watchful eye on the premises round-the-clock. With its advanced features like motion detection and live streaming, they can quickly address any potential security threats.
In another scenario, a small business owner uses Innocams to monitor their store remotely while attending important meetings or running errands. The peace of mind knowing that they can check in anytime, anywhere is priceless. Plus, the cost-effectiveness of this solution allows them to invest in other areas of their business.
Furthermore, a homeowner installs Innocams to keep an eye on their property while traveling for work. The ability to receive instant alerts and access footage from their smartphone provides unparalleled convenience and reassurance. This innovative technology truly transforms how we approach security and monitoring in our daily lives.
Potential Drawbacks of Using Innocams
While Innocams offers numerous benefits, it’s important to consider potential drawbacks when deciding if it’s the right choice for your security needs. One drawback is the reliance on a stable internet connection – any disruptions could impact live video streaming and alerts. Additionally, some users may have privacy concerns as surveillance cameras are constantly recording activities within their premises.
Another drawback is the initial setup process which may require technical expertise or professional assistance. This can add to the overall cost of implementing Innocams. Moreover, depending solely on camera footage might not always provide a complete picture of security incidents, as blind spots or technical malfunctions could occur.
Regular maintenance and software updates are essential to ensure optimal performance of Innocams systems over time. Failure to do so could lead to vulnerabilities in security coverage.
Conclusion: Is Innocams Right for You?
When considering the benefits of enhanced security, remote monitoring capabilities, and cost-effectiveness that Innocams offers, it becomes clear that this smart solution can be a valuable addition to your home or business. With easy setup and user-friendly features, Innocams provides peace of mind and convenience in one package. Whether you are looking to improve security measures or keep an eye on your property remotely, Innocams may just be the right choice for you. Consider integrating this innovative technology into your surveillance system and experience the advantages firsthand.
Hi, I am Saad Qureshi and I am working since 2017 in this field with 5 years of experience in SEO and Guest posting. My range of services includes Article Posting on Authority Sites.

You may like
HOME IMPROVEMENT
Essential Tips and Strategies for Securing Your Living Space
Published
5 months agoon
March 13, 2024By
Saad
Introduction to Home Security
Home is a sanctuary where we seek comfort, privacy, and, most importantly, safety. The evolution of home security is a testimony to the growing complexities of protecting this sanctuary. Gone are the days when a simple lock and key were sufficient. Modern homes require ever more sophisticated measures to combat potential risks. One significant aspect of contemporary home security revolves around access control systems Orlando, which offer scalability and customization to fit the needs of any household. These systems, while advanced, must be user-friendly and resilient against the tactics of modern-day intruders. Home security should empower residents, providing a sense of control and peace of mind.
Assessing Your Home’s Security Needs
Understanding your home’s vulnerabilities is the first step towards fortification. Every household has unique weak spots that could be exploited. An objective security audit might encompass various factors, including geographical location, aesthetic features of the house, and the residents’ lifestyle. This goes beyond merely installing high-grade locks; it involves a detailed examination of every possible entry point, such as windows, garage doors, and utility access points. Considering the surrounding environment, such as lighting and foliage, is crucial in a holistic security strategy. Acknowledging privacy concerns is equally vital, especially in neighborhoods that sit closely together.
The Role of Locks in Home Security
Foundational to home security, locks must be robust and resilient. A high-quality lock can serve as both a physical barrier and a psychological deterrent to intruders. It is essential to know the types of locks available on the market, including deadbolts, padlocks, and smart locks, and to understand which type is best suited for different entry points in a home. One should consider locks certified by recognized standards organizations that have undergone rigorous testing for strength and durability. Seasonal changes and daily wear and tear may require occasional lock upgrades or replacements to ensure your security is not compromised.
Modern Lock Technologies Advancing Home Security
In today’s fast-paced world, convenience and security must go hand in hand. With the advent of smart locks and integrated home security systems, homeowners now have more control over their home security than ever. The synergy between mobile technology and security hardware has paved the way for systems that can be monitored and modified from anywhere at any time. These keyless entry systems provide a new level of convenience, eliminating the need for physical keys and allowing for remote access, which is a boon for those who travel often or have multiple people needing access. The key, however, lies in choosing reputable devices that maintain robust security standards to protect against cyber threats.
Beyond Locks: Comprehensive Security Systems
While locks are vital, a comprehensive approach to home security reaches further. Surveillance cameras and alarm systems have become increasingly accessible and are pivotal in monitoring and protecting residential spaces. Today’s security systems alert residents to intrusions and can be integrated with emergency services for prompt action. Innovations in this space include environmental monitoring for fire, water damage, and air quality, ensuring the home is guarded against various potential risks. Security systems can also deter crime by their mere presence, alerting would-be intruders that the house is well-protected and under watchful eyes.
Safe Habits for Home Occupants
At its core, home security is as much about habits and education as it is about hardware. Residents should be trained to take security measures, including locking doors and windows and being cautious about granting entry. These precautions extend to digital security, guarding against information that could be exploited for break-ins. One can share the importance of security protocols with housemates, reinforcing that a secure home is a shared responsibility. Alertness and communication within the family can prevent avoidable breaches and foster a safety culture.
Security & Scams
The Impact of Webcord Virus on Your Online Security
Published
5 months agoon
March 4, 2024By
Saad
Imagine logging into your favorite websites, only to realize that something sinister is lurking in the background. Webcord Virus, a silent threat to your online security, can wreak havoc on your devices without you even knowing it. In this blog post, we will delve into the depths of what Webcord Virus is and how you can protect yourself from its malicious intent. Stay tuned to safeguard your digital world!
What is Webcord Virus?
Webcord Virus is a type of malware that infiltrates your devices through malicious websites or downloads. It sneaks onto your system undetected, like a digital ninja, and starts its destructive mission. Once inside, Webcord Virus can gather sensitive information such as passwords, financial data, and personal details without you even realizing it.
This cunning virus can also track your online activities and browsing habits to send targeted ads or sell your information to third parties. Its stealthy nature makes it challenging to detect unless you have the right security measures in place. Webcord Virus operates quietly in the background, silently compromising your privacy and putting your online security at risk.
How Does Webcord Virus Work?
Webcord Virus operates stealthily, sneaking into your device through malicious downloads or phishing emails. Once inside, it starts to replicate and spread its code across your system like a digital parasite.
This malware is designed to lurk in the background, silently collecting sensitive information such as login credentials, financial details, and personal data. It can also give cybercriminals remote access to your device, allowing them to monitor your activities without detection.
Webcord Virus manipulates system settings and files, causing erratic behavior like sudden crashes or freezes. It can also redirect you to fake websites or bombard you with unwanted pop-up ads. Additionally, this virus can exploit vulnerabilities in software to further compromise your security.
By understanding how Webcord Virus operates, you can take proactive measures to safeguard your online presence and protect yourself from potential cyber threats.
The Dangers of Webcord Virus to Your Online Security
The Webcord Virus poses a significant threat to your online security by infiltrating your devices and stealing sensitive information. Once this malicious software infects your system, it can track your keystrokes, capturing passwords and personal data without your knowledge. This breach of privacy opens the door for cybercriminals to commit identity theft or financial fraud using the stolen information.
Moreover, the Webcord Virus can also give hackers remote access to your device, allowing them to spy on you through your webcam or microphone. This invasion of privacy can be incredibly unsettling and may compromise both personal and professional interactions. Additionally, this virus can slow down your device’s performance significantly as it runs in the background undetected.
It is crucial to recognize these dangers and take proactive measures to protect yourself from falling victim to the Webcord Virus.
Signs That Your Device is Infected with Webcord Virus
Are you experiencing unusual pop-up ads while browsing the web? This could be a sign that your device is infected with the Webcord virus. These intrusive ads may appear out of nowhere and disrupt your online activities.
Another common indicator of a Webcord virus infection is a sudden decrease in your device’s performance. If you notice that your computer or smartphone is running slower than usual, it could be due to the malicious software consuming system resources in the background.
Furthermore, unexpected changes to your browser settings, such as homepage modifications or new toolbars appearing without your consent, are red flags for a potential Webcord virus infection. Keep an eye out for these alterations as they can indicate unauthorized access to your device.
If you encounter frequent crashes or freezes on your device, it may also be attributed to the presence of the Webcord virus. These disruptions can disrupt your workflow and signify underlying security threats that need immediate attention.
Steps to Protect Yourself from Webcord Virus
To safeguard yourself from the Webcord Virus, it’s crucial to take proactive measures that can prevent its infiltration into your device. Start by ensuring your operating system and all applications are regularly updated with the latest security patches. These updates often contain fixes for vulnerabilities that malware like Webcord could exploit.
Another vital step is to be cautious when clicking on links or downloading attachments, especially from unfamiliar sources. Exercise caution even if the sender appears legitimate, as cybercriminals can easily impersonate trusted entities to trick users into infecting their devices.
Furthermore, consider installing reputable antivirus software that offers real-time scanning and protection against various types of malware, including the Webcord Virus. Regularly scan your device for any suspicious activity or files that could indicate a potential infection.
In addition, practice safe browsing habits by avoiding questionable websites and refraining from clicking on pop-up ads or engaging in risky online behavior. Remember that prevention is key when it comes to protecting your online security from threats like the Webcord Virus.
The Role of Antivirus Software in Preventing Webcord Virus
Antivirus software plays a crucial role in protecting your devices from the Webcord virus. These programs are designed to detect and eliminate malicious threats like Webcord before they can cause harm. By regularly scanning your system, antivirus software can identify any suspicious activity associated with the virus.
Additionally, antivirus programs often have real-time protection features that can block known malware strains like Webcord from infecting your device. They also provide regular updates to stay ahead of evolving cyber threats, ensuring that your system is always safeguarded against potential attacks.
Moreover, antivirus software offers additional security layers such as firewall protection and web filtering to prevent unauthorized access and block malicious websites hosting the Webcord virus. This comprehensive approach helps create a strong defense mechanism against online threats.
Investing in reputable antivirus software is essential for maintaining robust cybersecurity hygiene and preventing the infiltration of dangerous viruses like Webcord onto your devices.
Conclusion
Staying informed about potential online threats like Webcord Virus is crucial for safeguarding your online security. By understanding how this malware operates and being aware of the signs of infection, you can take proactive steps to protect yourself. Remember to keep your antivirus software up to date, practice safe browsing habits, and be cautious when downloading files or clicking on links. With vigilance and the right precautions in place, you can minimize the risk of falling victim to Webcord Virus and other cyber threats. Stay safe online!
Security & Scams
Understanding the Evolution and Importance of Zero Trust in Modern Cybersecurity
Published
5 months agoon
March 2, 2024By
Saad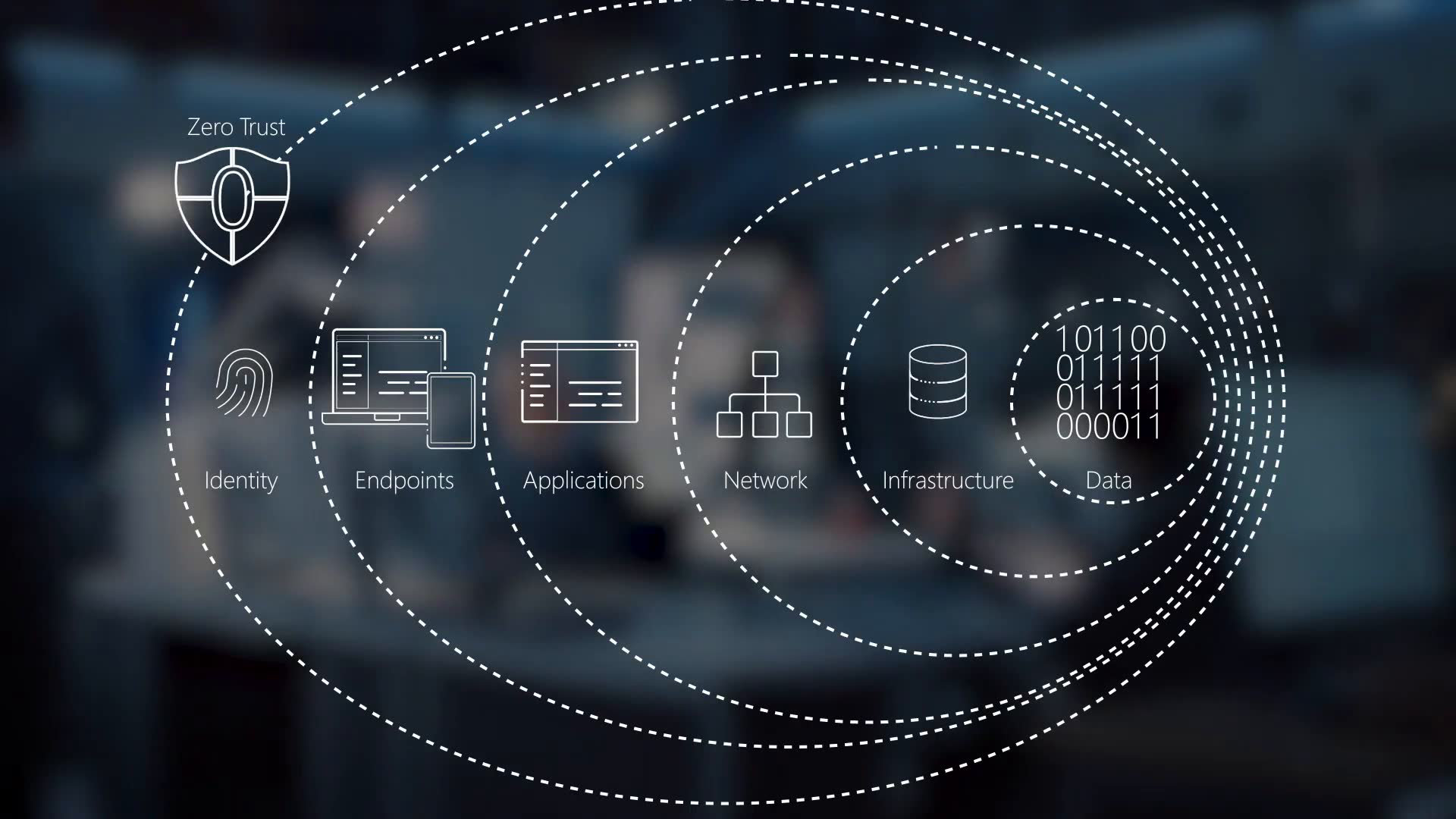
Introduction to Zero Trust Security
The cybersecurity domain is undergoing a paradigm shift by adopting the Zero Trust model, a framework with the precept that no one inside or outside the enterprise network is trustworthy without rigorous verification. The Zero Trust philosophy marks a clear departure from traditional security models, which worked under the assumption that everything within an organization’s network could be trusted. Zero Trust requires constant authentication, authorization, and validation of security configurations and is based on the idea of “never trust, always verify .”The sustainability and relevance of this model are evident in the way it accommodates contemporary digital practices such as remote work and reliance on cloud computing.
Embracing Zero Trust is not merely about adopting new technologies but signifies a more holistic rethinking of cybersecurity policy and structure. Organizations must pivot to the recognition that network defenses extend beyond maintaining a fortified boundary to include stringent internal controls. It effectively ends the era of broad Trust within the internal network and establishes minutely controlled access for every user, regardless of their perceived position or authority.
The Catalysts for Zero Trust Adoption
The shift towards Zero Trust did not happen in a vacuum. The surge in security breaches worldwide, clearly indicative of the vulnerabilities inherent in traditional perimeter-based security defenses, sparked an urgency for change. High-profile cyber-attacks and data breaches exemplify cyber adversaries’ innovative and sophisticated methods, compelling the adoption of more robust and resilient security frameworks like Zero Trust. These incidents accentuate the need for a more dynamic and adaptable approach to securing information assets.
In addition, the burgeoning adoption of cloud technologies and the rise of mobile and remote workforces have dissolved the traditional office perimeter. Businesses have increasingly recognized the need for security frameworks to safeguard assets beyond physical boundaries. Consequently, zero-trust models, which eschew the idea of a secure internal network, are welcomed as necessary for modern, distributed work environments.
Core Components of a Zero Trust Architecture
The steadfastness of Zero Trust security relies heavily on its core components, which enforce security protocols at every layer of the IT ecosystem. The first pillar, identity verification, entails the creation of comprehensive user profiles and leverages technologies like multi-factor authentication (MFA) to ensure that each access request is legitimate. Persistent device security is also vital, as endpoints represent gateways to network resources. Ensuring devices are secure and compliant before connecting significantly fortifies the network against invasive threats.
Another foundational element lies in meticulously designed network segmentation, which limits an attacker’s ability to traverse systems freely upon gaining access. By partitioning the network into discrete segments, security teams can isolate incidents and restrict the spread of potential breaches. These elements merge to form a framework that consistently validates user and device trustworthiness, substantially reducing an organization’s threat surface.
Zero Trust Implementation Challenges and Best Practices
Shifting to a Zero Trust model is often met with institutional inertia, representing a departure from established norms. Challenges include managing the complexity of redesigning network architecture and aligning the company culture to prioritize security. Skepticism from stakeholders is a common barrier, which can be mitigated by articulating the direct benefits of Zero Trust and demonstrating its necessity in the face of the modern cyber threat landscape.
A systematic approach to embracing Zero Trust is to start small, with a sector of the network or a specific asset type, and then scale up. Consistent policy enforcement across all network segments and frequent reassessments ensure the Zero Trust framework remains relevant and practical. Such vigilance pays dividends by creating a dynamic security posture capable of adapting to new challenges.
Case Studies: Zero Trust in Action
Nothing exemplifies the efficacy of a security concept better than its successful real-world application. Numerous case studies demonstrate how organizations from varied industries have embraced zero-trust principles to enhance their security posture. One particular example saw a significant financial institution overhaul its legacy systems to a zero-trust architecture, significantly decreasing the incidence and impact of security breaches. Through the Zero Trust lens, they adopted a more granular, risk-based approach to access control, which translated into heightened security and operational efficiency.
Another case study involving a healthcare provider highlighted the role of Zero Trust in protecting sensitive patient information. Implementing strict identity and access management policies ensured that only authorized personnel could access patient data, enhancing compliance with healthcare regulations and improving data security.
Zero Trust Security: The Significance of AI and Machine Learning
Zero-trust architectures, which offer better detection and response capabilities, are being created thanks to advances in artificial intelligence (AI) and machine learning (ML). These AI-powered security solutions can analyze vast amounts of data to identify abnormal patterns and potential threats faster and more accurately than ever. By leveraging AI-driven analytics, security teams can detect subtle indicators of compromise that might elude traditional security mechanisms. ML algorithms excel in environment pattern recognition, allowing for more refined access controls based on user behavior, location, and other contextual factors. Their predictive capabilities introduce a proactive rather than reactive approach to security, a cornerstone of the Zero Trust philosophy.
Zero Trust and Compliance: Navigating Legal Requirements
Adopting Zero Trust is primarily motivated by compliance with legal and regulatory frameworks in many industries. It’s true where data protection and privacy are concerned. These regulations often require strict access controls and auditability features, which Zero Trust models inherently provide by facilitating detailed visibility of who accesses what data and when; Zero Trust strengthens security and aids in meeting compliance obligations with less friction.
Future of Zero Trust: Predictions and Forward-Looking Trends
Zero Trust is anticipated to become integral to organizational security strategies as the security landscape evolves. With the proliferation of connected devices and the ever-expanding digital perimeter, embracing a security model that verifies every entity on the network becomes indispensable. Zero Trust cybersecurity predictions indicate that it is on track to become a standard, driven by a need for security that matches the complexity and dynamism of the digital age.
Common Misconceptions about Zero Trust
Zero Trust is often burdened by myths relating to its complexity and cost. While implementing any new model comes with its share of challenges, the perception that Zero Trust is out of reach for smaller organizations must be clarified. Adopting Zero Trust gradually, which is possible with careful planning and execution, can be advantageous for companies of all sizes. Attacks are growing in sophistication daily; investing in a sound security architecture like Zero Trust can significantly mitigate the risks and protect an organization’s valuable data and reputation.
Conclusion: Incorporating Zero Trust into Your Cybersecurity Strategy
As organizations grapple with the prevalence of cyber threats, fluid work environments, and rigorous compliance demands, Zero Trust stands out as a resilient, adaptable, and robust security framework. The journey towards embracing Zero Trust may be gradual, requiring a cultural shift and a reimagining of traditional security postures. Nevertheless, the rewards of enhanced defense mechanisms, regulatory compliance, and the ability to thwart sophisticated cyber adversaries contribute to a compelling argument for integrating Zero Trust into any modern cybersecurity strategy.
Security & Scams
The Power of 01174411569: Revolutionizing Communication
Published
5 months agoon
March 1, 2024By
Saad
In today’s fast-paced world, effective communication is key to success. Businesses and individuals alike are constantly seeking ways to improve their communication methods to stay ahead in their respective fields. One such innovative solution that has been gaining traction is 01174411569.
What is 01174411569?
01174411569 is a cutting-edge communication tool that allows users to connect with others seamlessly. Whether it’s for business meetings, virtual conferences, or casual catch-ups with friends and family, 01174411569 offers a wide range of features to enhance the communication experience.
How does 01174411569 work?
01174411569 utilizes advanced technology to enable users to communicate through voice, video, and text messages. Its user-friendly interface makes it easy for anyone to join a conversation with just a few clicks. Additionally, 01174411569 offers high-quality audio and video, ensuring crystal-clear communication even in low bandwidth conditions.
Benefits of using 01174411569
- Enhanced communication: 01174411569 provides a platform for users to communicate effectively, regardless of their location.
- Cost-effective: With 01174411569, users can save money on travel expenses and international calling rates.
- Increased productivity: By streamlining communication, 01174411569 helps teams collaborate more efficiently, leading to higher productivity levels.
How to use 01174411569 effectively
To make the most of 01174411569, it’s essential to familiarize yourself with its features and settings. Additionally, setting clear communication goals and establishing guidelines for its use can help ensure that 01174411569 is used effectively within your organization or personal life.
Common misconceptions about 01174411569
Despite its many benefits, there are some common misconceptions about 01174411569. One of the most common is that it is only suitable for large businesses. In reality, 01174411569 can be used by individuals and small businesses alike to improve their communication methods.
The future of 01174411569
As technology continues to evolve, so too will 01174411569. With new features and improvements constantly being developed, 01174411569 is poised to revolutionize the way we communicate in the future.
Case studies and success stories
Many businesses and individuals have already experienced the benefits of using 01174411569. Case studies and success stories highlight how 01174411569 has helped improve communication and collaboration, leading to tangible results.
FAQs about 01174411569
- What devices can I use 01174411569 on?
- Is 01174411569 secure?
- How much does 01174411569 cost?
- Can I use 01174411569 for personal use?
- How do I get started with 01174411569?
Conclusion
In conclusion, 01174411569 is a powerful communication tool that has the potential to transform the way we connect with others. Its innovative features and user-friendly interface make it a valuable asset for businesses and individuals alike. By embracing 01174411569, you can enhance your communication methods and stay ahead in today’s competitive world.
Trending
-
 ENTERTAINMENT5 months ago
ENTERTAINMENT5 months agoHBO Max TV Sign In Guide
-

 FASHION7 months ago
FASHION7 months agoJourney of Sandra Orlow From Aspiring Model to Internet Sensation
-

 TRAVEL6 months ago
TRAVEL6 months agoUnveiling the Beauty: A Closer Look at myfavouriteplaces.org Blog
-

 NEWS7 months ago
NEWS7 months agoBench Craft Company Lawsuit: A Comprehensive Analysis
-

 BUSINESS7 months ago
BUSINESS7 months agoChina SEO Xiaoyan: Pioneering the Path in Chinese Digital Marketing
-

 FASHION5 months ago
FASHION5 months agoThe Rise of Jeansato: A Revolutionary Denim Trend
-

 ENTERTAINMENT5 months ago
ENTERTAINMENT5 months agoGeekzilla Podcast: Navigating the Geek Cosmos
-

 TECH7 months ago
TECH7 months agoExploring Fibahub – Your Ultimate Solution for Seamless Communication
